Why Are Strings Immutable in Java? Discovering the Design Decisions
Why Are Strings Immutable in Java? Discovering the Design Decisions
Blog Article
The Advancement of Unalterable String Handling: A Crucial Element of Software Growth
In the elaborate world of software program growth, the handling of unalterable strings stands as a foundation that has undertaken significant advancement gradually. From its simple origins to the complicated challenges encountered in very early executions, the trip of immutable string control has been an important aspect of software application design. As we navigate through the historic landscape of this essential principle, mapping the improvements, security effects, and emerging trends, we find ourselves at a time where the intrinsic value of comprehending this evolution comes to be increasingly obvious.
Beginnings of Immutable Strings
When developers sought to improve the integrity and security of information dealing with systems,The idea of immutable strings traces back to the early days of programs languages. Unalterable strings describe strings that can not be transformed after they are produced. This fundamental principle was presented to deal with issues relating to information integrity and avoid unintentional alterations to essential information stored as strings.
In addition, unalterable strings add to boosting the overall safety of software program systems (Why are strings immutable in Java?). By protecting against unapproved parties from damaging delicate string information, unalterable strings help reduce the risk of data breaches and unapproved accessibility to secret information. This fundamental concept remains to play an essential function in contemporary programming languages and remains a foundation of durable and safe and secure software development practices
Early Challenges and Solutions
Navigating the landscape of early software program growth postured considerable hurdles in making sure the integrity and safety of data handling devices. Among the main difficulties in managing immutable strings was taking care of memory effectively. In early systems, memory allowance and deallocation were manual processes, leading to potential memory leakages and susceptabilities. Additionally, making sure that strings stayed unaltered confirmed to be intricate, specifically when multiple parts of the codebase needed to accessibility and change data.
To address these difficulties, designers started executing information encryption techniques to shield delicate information stored in immutable strings. By including file encryption and hashing methods into the handling of immutable strings, programmers considerably boosted the safety and security and reliability of data within software program systems.
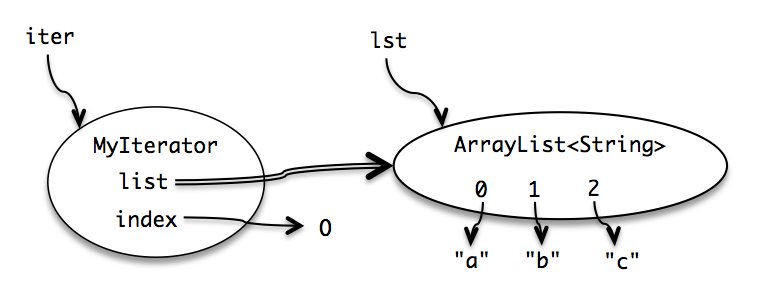
Advancements in String Immutability
In software growth, a significant advancement in the handling of immutable strings has actually arised via advancements in data encryption and hashing methods. By employing protected hash algorithms like SHA-256 or cryptographic site link methods such as AES file encryption, developers can guarantee that sensitive information stored in immutable strings remains protected and tamper-proof. These improvements have actually bolstered the integrity and confidentiality of information within applications, especially in sectors where information security is vital, such as money, health care, and cybersecurity.
Furthermore, advancements in string immutability have led the way for boosted efficiency optimization. Unalterable strings enable extra efficient memory administration and caching techniques, lowering the overhead connected with constant string manipulations (Why are strings immutable in Java?). This optimization not only improves the total responsiveness of software applications however also adds to better scalability and source usage
Security Ramifications and Finest Practices
With the foundation laid by advancements in string immutability, understanding the safety and security implications and carrying out ideal practices becomes critical in protecting delicate data within software program applications. Unalterable strings play an important duty in improving safety and security by avoiding unauthorized alterations to data, making sure information honesty throughout the application's lifecycle. By utilizing unalterable strings, designers can mitigate typical susceptabilities such as injection attacks, buffer overflows, and information meddling, which are frequently exploited by destructive actors to jeopardize systems.
To improve safety better, best methods ought to be adhered to when managing sensitive details. This includes securing data at remainder and en route, executing appropriate accessibility controls, utilizing safe coding techniques, and frequently upgrading software application parts to patch well-known vulnerabilities. In addition, developers ought to follow the concept of the very least opportunity, ensuring that only required consents are approved to customers and procedures. best site By including these security actions and best techniques into software application development procedures, organizations can better protect their data assets and reduce the threat of safety and security violations and information leakages.
Future Patterns in String Handling
In the middle of the ever-evolving landscape of software advancement, the trajectory of string handling is positioned to witness significant improvements and advancements. Designers are checking out brand-new algorithms and information frameworks to boost the rate and effectiveness of string operations.
Moreover, another fad coming up is the combination of man-made intelligence (AI) and artificial intelligence (ML) in string managing tasks. AI-powered devices are being established to automate and enhance numerous string manipulation processes, website here causing boosted productivity and precision in software growth operations.
In addition, there is a growing focus on enhancing the safety and security aspects of string managing with progressed file encryption strategies and protected coding practices. As cyber threats remain to evolve, guaranteeing the stability and privacy of information within strings is ending up being a top priority for programmers. By embracing robust protection measures, such as encryption at rest and in transportation, programmers can alleviate the dangers connected with string adjustment vulnerabilities.
Verdict
In final thought, the evolution of immutable string handling has actually been a vital aspect of software application development, beginning from its origins to the developments made recently. Early difficulties have been dealt with via cutting-edge services, leading to better safety methods in managing strings. It is essential for programmers to stay updated on the most recent trends in string immutability to ensure the robustness and safety of their software program applications.
Unalterable strings refer to strings that can not be transformed after they are developed. Why are strings immutable in Java?. By preventing unapproved parties from meddling with delicate string data, immutable strings help alleviate the threat of information breaches and unauthorized accessibility to personal details. By integrating file encryption and hashing approaches right into the handling of unalterable strings, designers dramatically boosted the security and integrity of information within software program systems
Immutable strings enable for much more effective memory monitoring and caching strategies, decreasing the overhead connected with constant string adjustments. Immutable strings play a vital duty in boosting security by stopping unauthorized alterations to information, ensuring data integrity throughout the application's lifecycle.
Report this page